Analysis of cybersecurity vulnerabilities of the smart grid using IEC61850 standard
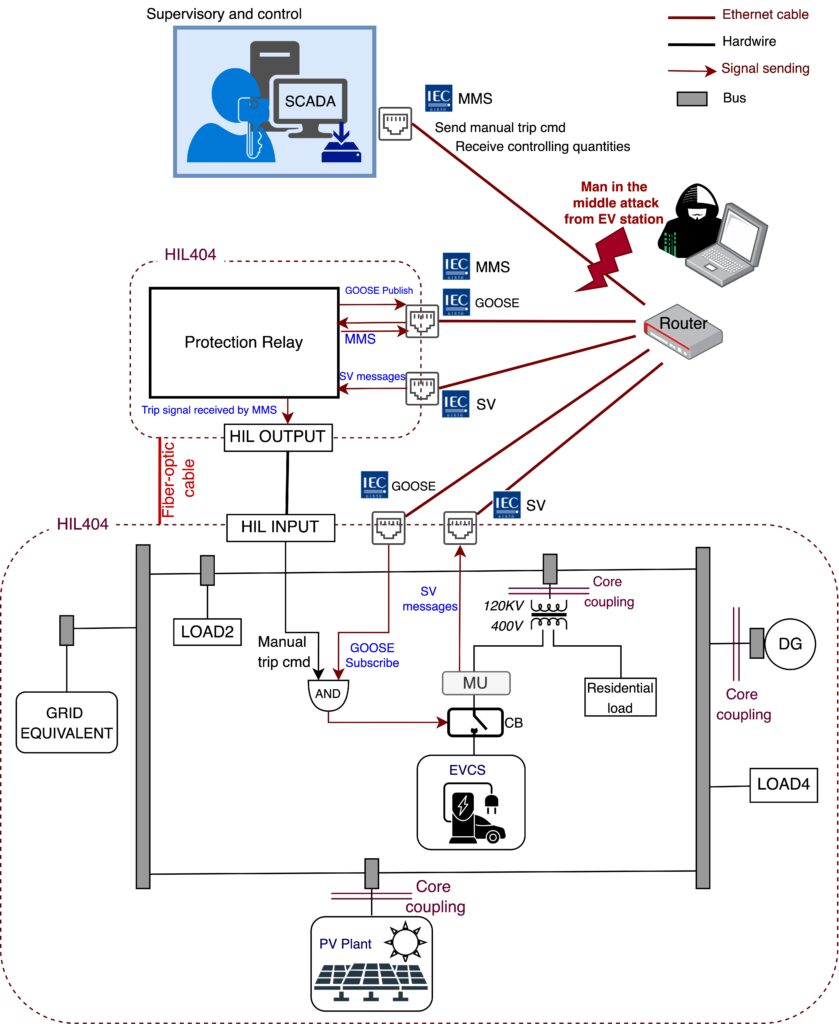
The goal of this activity was to recreate a given substation using built-in IEC61850 communication protocols in typhoon HIL and build a Hardware-in-the-loop testbed setup to investigate cyber-attack vulnerabilities by studying the application of MMS, GOOSE, and SV messages in Intelligent Electronic Devices (IEDs). The following listed measures are taken to fulfill this goal.
1.An emulated IED is designed to recreate the physical IEDs in a typhoon HIL device to be used in scenarios with multiple IEDs. This emulated IED is a digital twin of a generic protection IED.
- A microgrid equipped with IEC61850 protocols in different application layers is designed (GOOSE for interlock and protection messages, MMS for supervisory messages, and SV for sending measured signals to protection IEDs)
- The microgrid is also equipped with an EV aggregator that acts as an interface between the grid and EVs and takes the information of EV drivers, such as charging power demand and connection time via the smart meter and sends them to the grid operators. These exchanges of information are done via IEC61850 protocols too.
- A set of fault protection scenarios are performed using the emulated IED and physical IEDs, and the introduced delays related to each protocol implemented are investigated under different conditions. Also, functionality and robustness of the protection mechanisms and communication protocols are confirmed.
- Finally, vulnerability of smart grids that use IEC61850 as their primary communication protocol to data injection attacks such as man-in-the-middle and DDOS attack are studied. This study includes sniffing the local network, capturing and monitoring the exchanged packets and injecting the spoofed data with the same structure into the network to conduct false data injection attacks on the supervisory unit.
Results:
- Vulnerabilities to false data injection attacks in GOOSE, SV messages, and MMS protocols are confirmed provided that having physical access to the LAN network.
- Some countermeasures are suggested to deploy in the areas connected to the LAN network and accessible by public such EV charging stations.